The 2017 Linux Security Summit (LSS) was held last month in Los Angeles over the 14th and 15th of September. It was co-located with Open Source Summit North America (OSSNA) and the Linux Plumbers Conference (LPC).

LSS 2017
Once again we were fortunate to have general logistics managed by the Linux Foundation, allowing the program committee to focus on organizing technical content. We had a record number of submissions this year and accepted approximately one third of them. Attendance was very strong, with ~160 attendees — another record for the event.

LSS 2017 Attendees
On the day prior to LSS, attendees were able to access a day of LPC, which featured two tracks with a security focus:
Many thanks to the LPC organizers for arranging the schedule this way and allowing LSS folk to attend the day!
Realtime notes were made of these microconfs via etherpad:
I was particularly interested in the topic of better integrating LSM with containers, as there is an increasingly common requirement for nesting of security policies, where each container may run its own apparently independent security policy, and also a potentially independent security model. I proposed the approach of introducing a security namespace, where all security interfaces within the kernel are namespaced, including LSM. It would potentially solve the container use-cases, and also the full LSM stacking case championed by Casey Schaufler (which would allow entirely arbitrary stacking of security modules).
This would be a very challenging project, to say the least, and one which is further complicated by containers not being a first class citizen of the kernel. This leads to security policy boundaries clashing with semantic functional boundaries e.g. what does it mean from a security policy POV when you have namespaced filesystems but not networking?
Discussion turned to the idea that it is up to the vendor/user to configure containers in a way which makes sense for them, and similarly, they would also need to ensure that they configure security policy in a manner appropriate to that configuration. I would say this means that semantic responsibility is pushed to the user with the kernel largely remaining a set of composable mechanisms, in relation to containers and security policy. This provides a great deal of flexibility, but requires those building systems to take a great deal of care in their design.
There are still many issues to resolve, both upstream and at the distro/user level, and I expect this to be an active area of Linux security development for some time. There were some excellent followup discussions in this area, including an approach which constrains the problem space. (Stay tuned)!
A highlight of the TPMs session was an update on the TPM 2.0 software stack, by Philip Tricca and Jarkko Sakkinen. The slides may be downloaded here. We should see a vastly improved experience over TPM 1.x with v2.0 hardware capabilities, and the new software stack. I suppose the next challenge will be TPMs in the post-quantum era?
There were further technical discussions on TPMs and container security during subsequent days at LSS. Bringing the two conference groups together here made for a very productive event overall.

TPMs microconf at LPC with Philip Tricca presenting on the 2.0 software stack.
This year, due to the overlap with LPC, we unfortunately did not have any LWN coverage. There are, however, excellent writeups available from attendees:
There were many awesome talks.
The CII Best Practices Badge presentation by David Wheeler was an unexpected highlight for me. CII refers to the Linux Foundation’s Core Infrastructure Initiative , a preemptive security effort for Open Source. The Best Practices Badge Program is a secure development maturity model designed to allow open source projects to improve their security in an evolving and measurable manner. There’s been very impressive engagement with the project from across open source, and I believe this is a critically important effort for security.
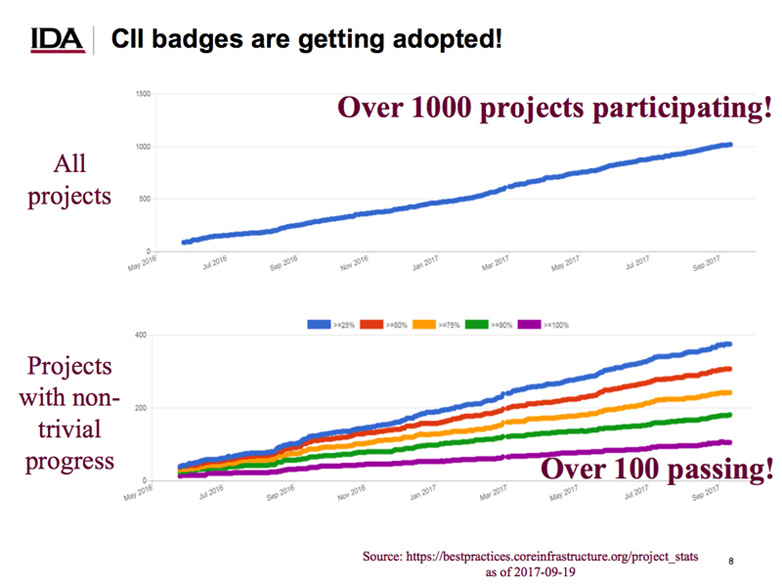
CII Bade Project adoption (from David Wheeler’s slides).
During Dan Cashman’s talk on SELinux policy modularization in Android O, an interesting data point came up:
We of course expect to see application vulnerability mitigations arising from Mandatory Access Control (MAC) policies (SELinux, Smack, and AppArmor), but if you look closely this refers to kernel vulnerabilities. So what is happening here? It turns out that a side effect of MAC policies, particularly those implemented in tightly-defined environments such as Android, is a reduction in kernel attack surface. It is generally more difficult to reach such kernel vulnerabilities when you have MAC security policies. This is a side-effect of MAC, not a primary design goal, but nevertheless appears to be very effective in practice!
Another highlight for me was the update on the Kernel Self Protection Project lead by Kees, which is now approaching its 2nd anniversary, and continues the important work of hardening the mainline Linux kernel itself against attack. I would like to also acknowledge the essential and original research performed in this area by grsecurity/PaX, from which this mainline work draws.
From a new development point of view, I’m thrilled to see the progress being made by Mickaël Salaün, on Landlock LSM, which provides unprivileged sandboxing via seccomp and LSM. This is a novel approach which will allow applications to define and propagate their own sandbox policies. Similar concepts are available in other OSs such as OSX (seatbelt) and BSD (pledge). The great thing about Landlock is its consolidation of two existing Linux kernel security interfaces: LSM and Seccomp. This ensures re-use of existing mechanisms, and aids usability by utilizing already familiar concepts for Linux users.
Overall I found it to be an incredibly productive event, with many new and interesting ideas arising and lots of great collaboration in the hallway, lunch, and dinner tracks.
Slides from LSS may be found linked to the schedule abstracts.
We did not have a video sponsor for the event this year, and we’ll work on that again for next year’s summit. We have discussed holding LSS again next year in conjunction with OSSNA, which is expected to be in Vancouver in August.
We are also investigating a European LSS in addition to the main summit for 2018 and beyond, as a way to help engage more widely with Linux security folk. Stay tuned for official announcements on these!
Thanks once again to the awesome event staff at LF, especially Jillian Hall, who ensured everything ran smoothly. Thanks also to the program committee who review, discuss, and vote on every proposal, ensuring that we have the best content for the event, and who work on technical planning for many months prior to the event. And of course thanks to the presenters and attendees, without whom there would literally and figuratively be no event :)
See you in 2018!





