According to Red Hat Security Advisory RHSA-2008-0002, a recently discovered stack overflow flaw in OpenPegasus is mitigated by standard SELinux targeted policy in RHEL4 and RHEL5:
… an unauthenticated remote user could trigger this flaw and potentially execute arbitrary code with root privileges. (CVE-2008-0003)
Note that the tog-pegasus packages are not installed by default on Red Hat Enterprise Linux. The Red Hat Security Response Team believes that it would be hard to remotely exploit this issue to execute arbitrary code, due to the default SELinux targeted policy on Red Hat Enterprise Linux 4 and 5, and the SELinux memory protection tests enabled by default on Red Hat Enterprise Linux.
The enhanced memory protection tests in RHEL5 contribute here to mitigation.
On a related note, Mark Cox has just published an updated grid of vulnerability and threat mitigation features in RHEL and Fedora. Fedora 8, being the most recent distro listed, has the greatest number of these features.
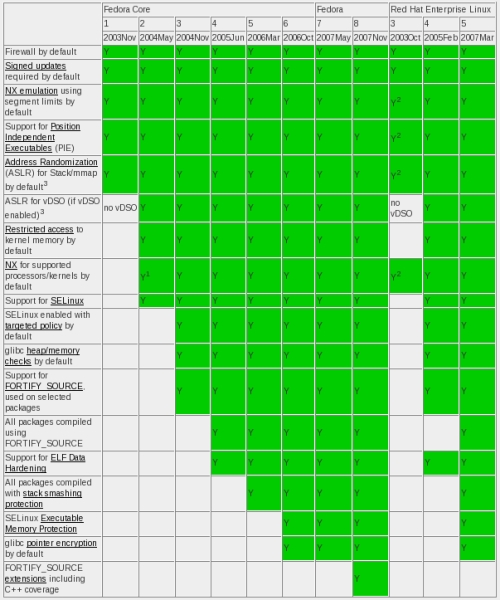
Btw, for those able to attend FUDCon in Raleigh over the weekend, there will be a few SELinux folk around to answer questions, listen to feedback etc.
Update:
Someone asked for more Fedora-specific information to compare with other distributions. Here’s a well-maintained page on Fedora Security Features.