With the recent news of multiple vulnerabilities in Adobe flash and PDF software, folk running Fedora 10 may wish to consider using SELinux to confine browser plugins.
Dan Walsh has previously implemented SELinux lockdown for browser plugins via nspluginwrapper, as discussed here. Unfortunately, this has been disabled by default, due to a clash with the mozplugger package, which uses nspluginwrapper to launch applications inside the browser.
Personally, I’m happy to have OpenOffice or similar open up in a separate window, using the standard Firefox mechanism for doing so, especially if it means I’m able to keep browser plugin confinement enabled.
Here’s what I did:
# yum remove mozplugger
# setsebool -P allow_unconfined_nsplugin_transition=on
# setsebool -P allow_nsplugin_execmem=off
# setsebool -P nsplugin_can_network=off
This of course removes mozplugger, but I don’t seem to need it. When downloading a PDF, for example, Firefox prompts if I want to open it with evince, and provides me with an option to always do that without further prompting. YMMV.
The setsebool commands change several nspluginwrapper options in SELinux, while the -P option ensures that the changes persist across reboots (see setsebool(8)).
Detailed explanation:
- Enabling
allow_unconfined_nsplugin_transition ensures that nspluginwrapper transitions to a new security label when running a plugin, so that special security policy can be applied to it. This is required for any useful effect.
- Disabling
allow_nsplugin_execmem ensures that memory protections are being enforced to prevent plugins from executing code on the stack and in mapped memory.
- Disabling
nsplugin_can_network prevents plugins from connecting to anything other than reserved ports. Apparently, this may upset some flash code which wants to call home (you’d be surprised how much of this goes on, or perhaps not), so you may want to leave this as-is, or at least keep an eye on the messages from setroubleshoot.
Note that if you do run into problems, you can put SELinux into permissive mode rather than disabling it, which will at least provide some useful logging information (and feel free to post questions to the fedora-selinux-list).
Btw, here’s how to configure SELinux for permissive mode:
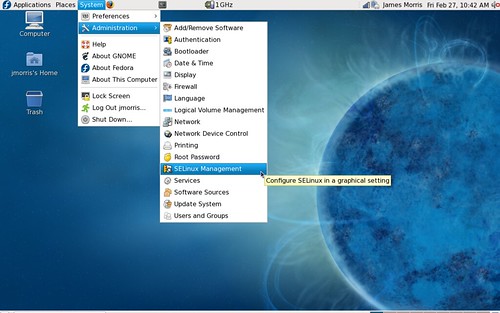
System -> Administration -> SELinux Management
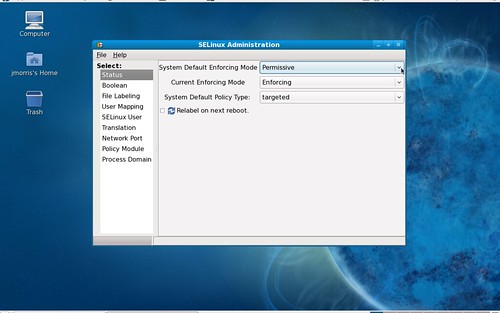
Set ‘System Default Enforcing Mode’ to ‘Permissive’
And you’re done.
A bugzilla ticket has been opened on the issue of finding a long-term solution which allows both mozplugger and plugin confinement to co-exist, but unfortunately, users currently need to decide whether they prefer increased security or a more Windows-like experience, with the latter as the default.


