Today was the last day of the Linux Plumbers Conference, which overall seems to have gone really well. Certainly it exceeded my expectations, which were already pretty high. In my view, the conference was distinctive in that it was totally developer-focused and collaborative, with no thinly-disguised marketing talks.
The atmosphere was relaxed, and not overly structured, which allowed for a lot of useful ad-hoc discussions between developers working in different areas of the OS. An example was Arjan’s talk on achieving a five-second boot, which itself was very interesting and entertaining, but was also followed by a lunch session with a bunch of distro maintainers to work out various specifics. It seems that a small arms race has been launched between Fedora & Ubuntu on who can first get the default install to a five second boot.
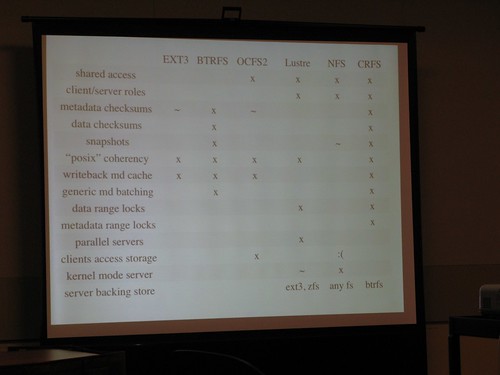
I was interested to catch up on the latest file system developments, and caught the updates on btrfs and crfs by their respective authors, Chris Mason & Zach Brown. The disk format for btrfs will be locked in before the end of the year, according to Chris, to encourage more developers and users to start playing with it. crfs is looking increasingly impressive as a small-scale, fast, reliable and sane networked file system: I grabbed a photo of the slide comparing it with other network filesystems:
Other photos I took at the conference are here.
It was really great to catch up with so many people I work with over the net, and also finally meeting some people I must have known for more than a decade but still never met in person — possibly due to this being the first Linux conference I’ve attended in the US.
During the closing, Kristen Accardi did a brief survey on several aspects of the conference, and it seems that virtually everyone was happy with it. I think the conference has a bright future, as it seems to have filled a now obvious need for a place where a cross-section of mainline Linux developers can meet up specifically to solve problems.