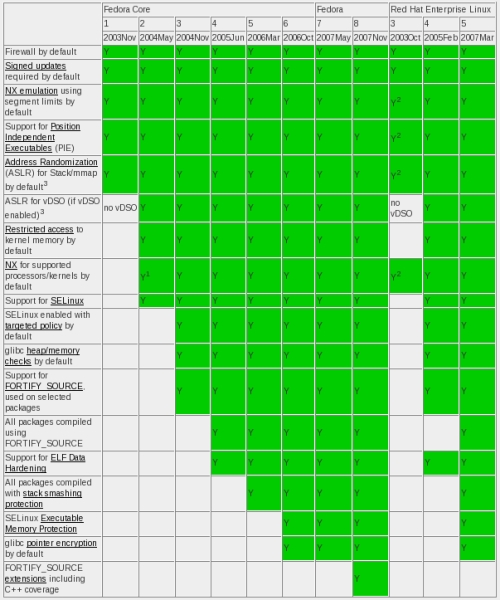
Fedora 8 now has support for Dan Walsh’s SELinux kiosk mode, or xguest, which he has previously described in some detail.
The good news is that it’s utterly simple to use:
- Upgrade to the very latest Fedora 8 — simply ensure you have run:
# yum update
- Install the xguest package and necessary dependencies:
# yum install xguest
- Ensure you’re running SELinux in enforcing mode:
# getenforce
Enforcing - Log out from X, and you should see a new “X Guest User” user in the GDM welcome screen:
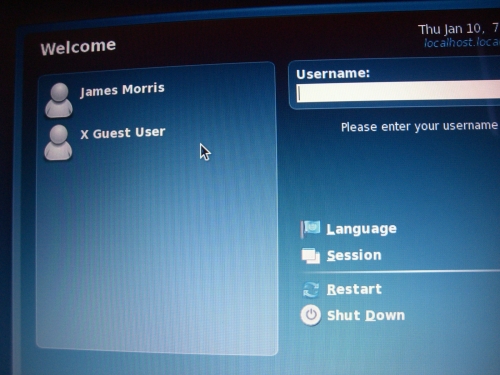
- Click on the X Guest User account, and you will be logged straight into a GNOME session.
The GNOME session will run as a very tightly locked down SELinux account, which can only be accessed via GDM. It is essentially authorized only to surf the web.
PAM namespace is utilized so that the session has private views of shared writable filesystem space (e.g. /tmp), while Sabayon is used to load a custom GNOME configuration.
Any local changes made by the user, such as writes to $home or their desktop settings will be lost after they log out.
Thomas Mraz’s PAM SELinux permit package ensures that the xguest account is only active in enforcing mode, to ensure the account cannot be used to attack the system if it is in permissive mode.
Further technical detail may be found in the package’s README file.
Where would you use this? Dan has found it useful for family members with various levels of computer skill, while I can imagine that xguest would also be quite handy for things like LUG events, conference booths, training, Linux demonstrations, information kiosks etc.
If you come up with any cool uses, or enhancements, please let us know.
Enjoy!